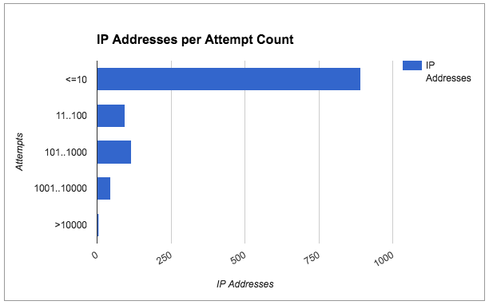
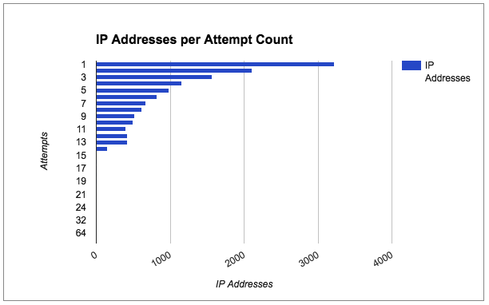
US hospitals lack new technologies and best practices to defend against threats, new report says.
Some 93 major cyberattacks hit healthcare organizations this year, up from 57 in 2015, new research shows.
TrapX Labs, a division of TrapX Security, found this 63% increase in attacks on the healthcare industry for the period between January 1, 2016 and December 12. Some may have been ongoing prior to Jan. 1, but for consistency, researchers only used official reporting dates to the Department of Health and Human Services, Office of Civil Rights (HHS OCR).
Among the largest attacks were those on Banner Health (3.6M records), Newkirk Products (3.4M records), 21st Century Oncology (2.2M records), and Valley Anesthesiology Consultants (0.88M records).
Sophisticated attackers are now responsible for 31% of all major HIPAA data breaches reported this year, a 300% increase over the past three years, according to the report. Cybercriminals were responsible for 10% of all major data breaches in 2014 and 21% in 2015.
Despite the rise in attacks, the number of records breached dropped to about 12,057,759. That said, so many millions of health records have been stolen that the value of individual records decreased this year, TrapX reported.
Researchers pinpointed two major trends from 2016: the continued discovery and evolution of medical device hijacking, which TrapX calls MEDJACK and MEDJACK.2, and the increase of ransomware across a variety of targets.
MEDJACK involves the use of backdoors in medical devices like diagnostic or life-support equipment. Hackers use emailed links, malware-equipped memory sticks, and corrupt websites to load tools into these devices, most of which run standard/older operating systems and proprietary software.
"Once inside the network, these attackers move laterally in search of high-profile targets from which they can ultimately exfiltrate intellectual property and patient data," says Moshe Ben-Simon, co-founder and VP of services at TrapX Labs.
One successful penetration is often enough to give hackers access to the network, where they can find unprotected devices to host attacks, chat with humans, and access information. It's difficult to mitigate the effects of MEDJACK; many hospitals don't even know it happens.
"Unfortunately, hospitals do not seem to be able to detect MEDJACK or remediate it," Simon explains. "The great majority of existing cyber-defense suites do not seem able to detect attackers moving laterally from these compromised devices."
Ransomware attacks on large and mid-sized healthcare organizations have also become more diverse. The financial depth and criticality of operations make them easy targets. It's one thing to close a business for one day; it's entirely different to force a hospital shutdown.
A July 2016 survey conducted by Solutionary discovered healthcare is the industry most frequently targeted by malware, accounting for 88% of all detections in Q2. Hackers target healthcare because organizations will usually pay ransom for valuable patient data.
TrapX researchers predict ransomware will reach "unprecedented levels" next year as quick ROI, and easy access to untraceable money such as Bitcoin, make it easier for hackers to launch more attacks at once
'Hacking' 카테고리의 다른 글
| What is SQL injection (SQLi)? (0) | 2019.12.13 |
|---|---|
| What is SQL injection (SQLi)? (0) | 2019.12.13 |
| A Cybersecurity Christmas Story (0) | 2016.12.27 |
| Brute-Force Botnet Attacks Now Elude Volumetric Detection (0) | 2016.12.27 |
| Russian Hackers Run Record-Breaking Online Ad-Fraud Operation (0) | 2016.12.27 |