
Submission Summary:
- Submission details:
- Submission received: 22 April 2010, 21:45:06
- Processing time: 7 min 30 sec
- Submitted sample:
- File MD5: 0x504CB0E268EAB6F47BD35780C537BCB1
- File SHA-1: 0x8EA44DC3C9B379A0E580074C5C325797BFEE83B6
- Filesize: 95,819 bytes
- Alias:
- Trojan.Gen
 [Symantec]
[Symantec] - Trojan-GameThief.Win32.Magania.dbxc [Kaspersky Lab]
- New Malware.bx
 [McAfee]
[McAfee] - TrojanDropper:Win32/Frethog.K
 [Microsoft]
[Microsoft] - Dropper/Killav.95819 [AhnLab]
- Summary of the findings:
| What's been found | Severity Level |
| Downloads/requests other files from Internet. |  |
| Creates a startup registry entry. |  |
| Registers a 32-bit in-process server DLL. |  |
| Registers a Browser Helper Object (Microsoft's Internet Explorer plugin module). |  |
| Contains characteristics of an identified security risk. |  |
Technical Details:
 |
Possible Security Risk |
- Attention! Characteristics of the following security risks were identified in the system:
| Security Risk | Description |
Trojan-PWS.Magania.AHIW |
Trojan-PWS.Magania.AHIW is threat that tries to monitors user activities in hopes to obtain valuable information from the affected user, specifically gaming login informations. |
Trojan.Generic |
Common Components that may be used by Trojans Small, DRSN Search, Binet, Euniverse, Adrotator and Dloader among others. |
- Attention! The following threat categories were identified:
| Threat Category | Description |
 |
A malicious trojan horse or bot that may represent security risk for the compromised system and/or its network environment |
 |
A program that downloads files to the local computer that may represent security risk |
 |
File System Modifications |
- The following files were created in the system:
| # | Filename(s) | File Size | File Hash | Alias |
| 1 | %Windir%\AhnRpta.exe |
69,120 bytes | MD5: 0x388B8FBC36A8558587AFC90FB23A3B99 SHA-1: 0xED55AD0A7078651857BD8FC0EEDD8B07F94594CC |
(not available) |
| 2 | %System%\anhdo.exe | 159,024 bytes | MD5: 0xA7A748E6017E471FC36E9332627C147C SHA-1: 0x1FDF53F443BA029941D14BD3DB566FA0F7C069A5 |
Worm:Win32/Taterf.B [Microsoft] [Microsoft]packed with PE_Patch [Kaspersky Lab] |
| 3 | %System%\ansb10.dll %System%\ansb11.dll |
64,598 bytes | MD5: 0x34503D6515C78FE759986E73F2482B06 SHA-1: 0xB0D9857230D10193DC0BCE290866266248AADFC2 |
PWS:Win32/Frethog.gen!G [Microsoft] [Microsoft]packed with PE_Patch [Kaspersky Lab] |
| 4 | %System%\ansb20.dll | 78,270 bytes | MD5: 0x58DBD396A3DF3E1FB0B54EA57242555A SHA-1: 0x30597FA342034EB381EE117941F1BA343207BD91 |
PWS:Win32/OnLineGames.AH [Microsoft] [Microsoft]packed with PE_Patch [Kaspersky Lab] |
| 5 | [file and pathname of the sample #1] | 95,819 bytes | MD5: 0x504CB0E268EAB6F47BD35780C537BCB1 SHA-1: 0x8EA44DC3C9B379A0E580074C5C325797BFEE83B6 |
Trojan.Gen [Symantec] [Symantec]Trojan-GameThief.Win32.Magania.dbxc [Kaspersky Lab] New Malware.bx  [McAfee] [McAfee]TrojanDropper:Win32/Frethog.K  [Microsoft] [Microsoft]Dropper/Killav.95819 [AhnLab] |
| 6 | %System%\softqq0.dll |
64,521 bytes | MD5: 0x39D3F8C3E522F07803A629E68D0B2E35 SHA-1: 0x4C5CE618A8DF1C1E70EC579BB58BA12C2842B391 |
Downloader [Symantec] [Symantec]TrojanDownloader:Win32/Frethog.C  [Microsoft] [Microsoft]Win-Trojan/Killav.64521 [AhnLab] packed with PE_Patch [Kaspersky Lab] |
- Notes:
- %Windir% is a variable that refers to the Windows installation folder. By default, this is C:\Windows or C:\Winnt.
- %System% is a variable that refers to the System folder. By default, this is C:\Windows\System (Windows 95/98/Me), C:\Winnt\System32 (Windows NT/2000), or C:\Windows\System32 (Windows XP).
 |
Memory Modifications |
- There was a new process created in the system:
| Process Name | Process Filename | Main Module Size |
AhnRpta.exe |
%Windir%\ahnrpta.exe |
81,920 bytes |
- The following modules were loaded into the address space of other process(es):
| Module Name | Module Filename | Address Space Details |
softqq0.dll |
%System%\softqq0.dll |
Process name: explorer.exe Process filename: %Windir%\explorer.exe  Address space: 0x1E80000 - 0x1EA8000 |
| ansb10.dll | %System%\ansb10.dll | Process name: explorer.exe Process filename: %Windir%\explorer.exe  Address space: 0x22A0000 - 0x22D1000 |
softqq0.dll |
%System%\softqq0.dll |
Process name: dllhost.exe Process filename: %System%\dllhost.exe Address space: 0x2530000 - 0x2558000 |
softqq0.dll |
%System%\softqq0.dll |
Process name: IEXPLORE.EXE Process filename: %ProgramFiles%\internet explorer\iexplore.exe  Address space: 0x1500000 - 0x1528000 |
softqq0.dll |
%System%\softqq0.dll |
Process name: AhnRpta.exe Process filename: %Windir%\ahnrpta.exe  Address space: 0x10000000 - 0x10028000 |
softqq0.dll |
%System%\softqq0.dll |
Process name: VMwareUser.exe Process filename: %ProgramFiles%\vmware\vmware tools\vmwareuser.exe  Address space: 0x10000000 - 0x10028000 |
softqq0.dll |
%System%\softqq0.dll |
Process name: AhnRpta.exe Process filename: %Windir%\ahnrpta.exe  Address space: 0x890000 - 0x8B8000 |
- Notes:
- %ProgramFiles% is a variable that refers to the Program Files folder. A typical path is C:\Program Files.
 |
Registry Modifications |
- The following Registry Keys were created:
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\NOD32KVBIT
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{B03A4BE6-5E5A-483E-B9B3-C484D4B20B72}
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{B03A4BE6-5E5A-483E-B9B3-C484D4B20B72}\InprocServer32
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{B03A4BE6-5E5A-B9B3-483E-C484D4B20B72}
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{C8414FA0-BA90-4600-B7EA-0CEFAF5A0636}
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{C8414FA0-BA90-4600-B7EA-0CEFAF5A0636}\InprocServer32
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{C8414FA0-BA90-4600-B7EA-0CEFAF5A0636}\ProgID
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{C8414FA0-BA90-4600-B7EA-0CEFAF5A0636}\Programmable
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{C8414FA0-BA90-4600-B7EA-0CEFAF5A0636}\VersionIndependentProgID
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj\CurVer
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj.1
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj.1\CLSID
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{C8414FA0-BA90-4600-B7EA-0CEFAF5A0636}
- The newly created Registry Values are:
- [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\NOD32KVBIT]
- KVBIT_2 = "xxxkkmm"
- [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{B03A4BE6-5E5A-483E-B9B3-C484D4B20B72}\InprocServer32]
- (Default) = "%System%\softqq0.dll"
- ThreadingModel = "Apartment"
- [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{B03A4BE6-5E5A-B9B3-483E-C484D4B20B72}]
- VcbitExeModuleName = "[file and pathname of the sample #1]"
- VcbitDllModuleName = "%System%\softqq0.dll"
- VcbitSobjEventName = "CVBASDDOOPADSAMN_0"
- [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{C8414FA0-BA90-4600-B7EA-0CEFAF5A0636}\VersionIndependentProgID]
- (Default) = "IEHlprObj.IEHlprObj"
- [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{C8414FA0-BA90-4600-B7EA-0CEFAF5A0636}\ProgID]
- (Default) = "IEHlprObj.IEHlprObj.1"
- [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{C8414FA0-BA90-4600-B7EA-0CEFAF5A0636}\InprocServer32]
- (Default) = "%System%\ansb20.dll"
- ThreadingModel = "Apartment"
- [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{C8414FA0-BA90-4600-B7EA-0CEFAF5A0636}]
- (Default) = "IEHlprObj Class"
- [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj\CurVer]
- (Default) = "IEHlprObj.IEHlprObj.1"
- [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj]
- (Default) = "IEHlprObj Class"
- [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj.1\CLSID]
- (Default) = "{C8414FA0-BA90-4600-B7EA-0CEFAF5A0636}"
- [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj.1]
- (Default) = "IEHlprObj Class"
- [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks]
- {B03A4BE6-5E5A-483E-B9B3-C484D4B20B72} = "hook dll rising"
- [HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
- anhdo = "%System%\anhdo.exe"
so that anhdo.exe runs every time Windows starts
 |
Other details |
- Analysis of the file resources indicate the following possible country of origin:
 |
China |
- There was registered attempt to establish connection with the remote host. The connection details are:
| Remote Host | Port Number |
| 114.31.57.82 | 80 |
- The data identified by the following URLs was then requested from the remote web server:
- http://bebehouse.geniemom.com/images_old/board/play.txt
- http://bebehouse.geniemom.com/images_old/board/copy.rar
All content ("Information") contained in this report is the copyrighted work of Threat Expert Ltd and its associated companies ("ThreatExpert") and may not be copied without the express permission of ThreatExpert.
The Information is provided on an "as is" basis. ThreatExpert disclaims all warranties, whether express or implied, to the maximum extent permitted by law, including the implied warranties that the Information is merchantable, of satisfactory quality, accurate, fit for a particular purpose or need, or non-infringing, unless such implied warranties are legally incapable of exclusion. Further, ThreatExpert does not warrant or make any representations regarding the use or the results of the use of the Information in terms of their correctness, accuracy, reliability, or otherwise.
Copyright © 2010 ThreatExpert. All rights reserved.
'Hacking' 카테고리의 다른 글
| Java Applet Security Model (0) | 2010.04.23 |
|---|---|
| SSH JAVA APPLET http://javassh.org/space/start (1) | 2010.04.23 |
| Computer Security Consulting (0) | 2010.04.02 |
| Update Snort (0) | 2010.03.04 |
| BASE 2010.3.3. Wed (1) | 2010.03.04 |
 Install or update the rules.
Install or update the rules.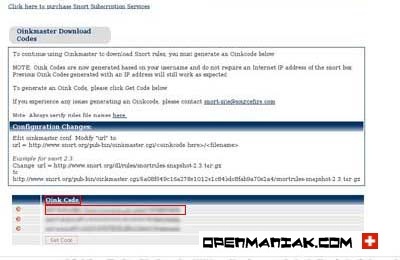



 TMACv5_R3_Setup(2).zip
TMACv5_R3_Setup(2).zip

