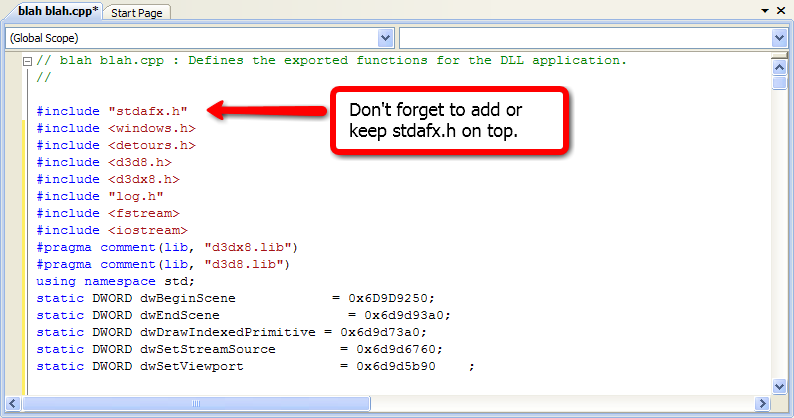
Code:
/*creds to me,Roverturbo,Azorbix,Frit0 ,unreal*/
#include <windows.h>
#include <detours.h>
#include <d3d8.h>
#include <d3dx8.h>
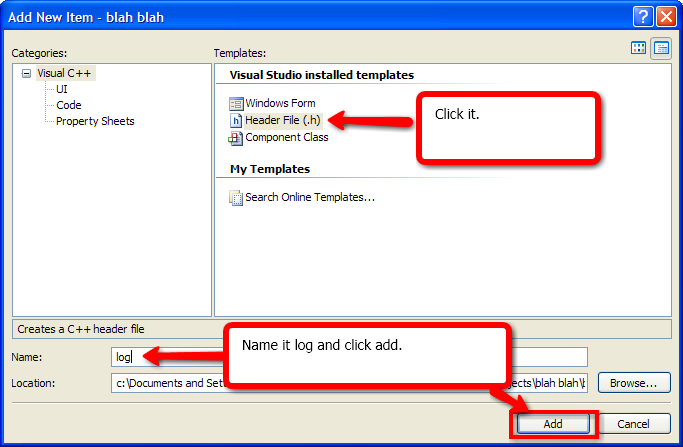
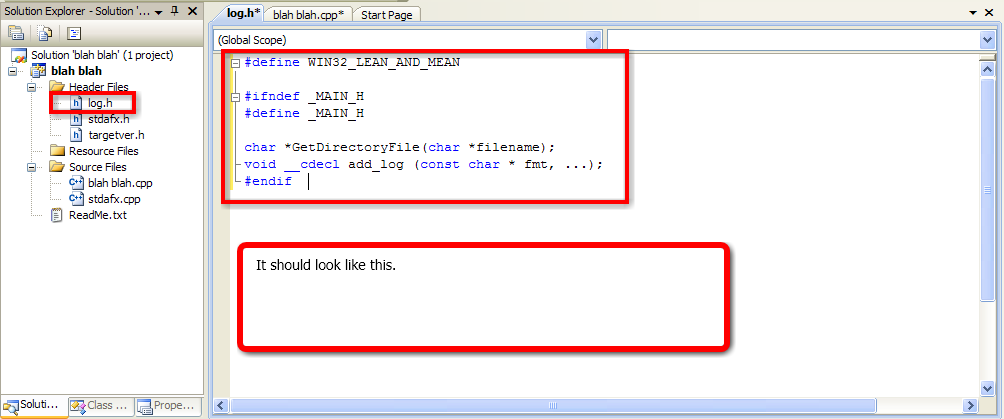
#include "log.h"
#include <fstream>
#include <iostream>
#pragma comment(lib, "d3dx8.lib")
#pragma comment(lib, "d3d8.lib")
using namespace std;
static DWORD dwBeginScene = 0x6D9D9250;
static DWORD dwEndScene = 0x6d9d93a0;
static DWORD dwDrawIndexedPrimitive = 0x6d9d73a0;
static DWORD dwSetStreamSource = 0x6d9d6760;
static DWORD dwSetViewport = 0x6d9d5b90 ;
int m_Stride;
int texnum;
int nNumVertices;
int nPrimitiveCount;
LPDIRECT3DTEXTURE8 Red,Yellow,Green,Blue,Purple,Pink,Orange;
bool Color = true;
bool Logger = false;
ofstream ofile;
char dlldir[320];
float ScreenCenterX = 0.0f;
float ScreenCenterY = 0.0f;
bool xhair = false;
bool WallHack = false;
bool WallHack2 = false;
HANDLE hand1 =NULL;
HANDLE hand2 =NULL;
DWORD bytes;
//Logger
int texarray[1000];
int arraycounter;
int delarray[500];
int dcount;
unsigned int arrc;
int i=0;
D3DCOLOR redt = D3DCOLOR_XRGB( 255, 0, 0 );
char *GetDirectoryFile(char *filename)
{
static char path[320];
strcpy(path, dlldir);
strcat(path, filename);
return path;
}
void __cdecl add_log (const char *fmt, ...)
{
if(ofile != NULL)
{
if(!fmt) { return; }
va_list va_alist;
char logbuf[256] = {0};
va_start (va_alist, fmt);
_vsnprintf (logbuf+strlen(logbuf), sizeof(logbuf) - strlen(logbuf), fmt, va_alist);
va_end (va_alist);
ofile << logbuf << endl;
}
}
HRESULT GenerateTexture(IDirect3DDevice8 *pD3Ddev, IDirect3DTexture8 **ppD3Dtex, DWORD colour32)
{
if( FAILED(pD3Ddev->CreateTexture(8, 8, 1, 0, D3DFMT_A4R4G4B4, D3DPOOL_MANAGED, ppD3Dtex)) )
return E_FAIL;
WORD colour16 = ((WORD)((colour32>>28)&0xF)<<12)
|(WORD)(((colour32>>20)&0xF)<<8)
|(WORD)(((colour32>>12)&0xF)<<4)
|(WORD)(((colour32>>4)&0xF)<<0);
D3DLOCKED_RECT d3dlr;
(*ppD3Dtex)->LockRect(0, &d3dlr, 0, 0);
WORD *pDst16 = (WORD*)d3dlr.pBits;
for(int xy=0; xy < 8*8; xy++)
*pDst16++ = colour16;
(*ppD3Dtex)->UnlockRect(0);
return S_OK;
}
//=================================EndScene_Start=================================================================================//
typedef HRESULT ( WINAPI* oEndScene ) ( LPDIRECT3DDEVICE8 pDevice );
oEndScene pEndScene;
HRESULT WINAPI myEndScene(LPDIRECT3DDEVICE8 pDevice)
{
if(Color)
{
GenerateTexture(pDevice, &Red, D3DCOLOR_ARGB (255 , 255 , 0 , 0 ));
GenerateTexture(pDevice, &Yellow, D3DCOLOR_ARGB (255 , 255 , 255 , 0 ));
GenerateTexture(pDevice, &Green, D3DCOLOR_ARGB (255 , 0 , 255 , 0 ));
GenerateTexture(pDevice, &Blue, D3DCOLOR_ARGB (255 , 0 , 0 , 255 ));
GenerateTexture(pDevice, &Purple, D3DCOLOR_ARGB (255 , 102 , 0 , 153 ));
GenerateTexture(pDevice, &Pink, D3DCOLOR_ARGB (255 , 255 , 20 , 147 ));
GenerateTexture(pDevice, &Orange, D3DCOLOR_ARGB (255 , 255 , 165 , 0 ));
Color=false;
}
if(xhair)
{
D3DRECT rec2 = {ScreenCenterX-20, ScreenCenterY, ScreenCenterX+ 20, ScreenCenterY+2};
D3DRECT rec3 = {ScreenCenterX, ScreenCenterY-20, ScreenCenterX+ 2,ScreenCenterY+20};
pDevice->Clear(1, &rec2, D3DCLEAR_TARGET,redt, 0, 0);
pDevice->Clear(1, &rec3, D3DCLEAR_TARGET,redt, 0, 0);
}
//=============================================UnHooK_Start===================================================//
if((GetAsyncKeyState(VK_F5)&1))
{
int end =NULL;
int dip =NULL;
int svp =NULL;
int sss =NULL;
BYTE Unhook[5] = {0x8B,0xFF,0x55,0x8B,0xEC};//Original Function Bytes.
hand1 = GetCurrentProcess();
DWORD dwmodualBase=(DWORD)GetModuleHandle("d3d8.dll");
end = 0x6d9d93a0;
dip = 0x6d9d73a0;
svp = 0x6d9d5b90;
sss = 0x6d9d6760;
WriteProcessMemory(hand1, (void*) end, Unhook, 5, &bytes);
WriteProcessMemory(hand1, (void*) dip, Unhook, 5, &bytes);
WriteProcessMemory(hand1, (void*) svp ,Unhook, 5, &bytes);
WriteProcessMemory(hand1, (void*) sss,Unhook, 5, &bytes);
}
//=========================================UnHook_End=========================================================//
if((GetAsyncKeyState(VK_F1)&1)){xhair=!xhair;}
if((GetAsyncKeyState(VK_F2)&1)){WallHack=!WallHack;}
return pEndScene(pDevice);
}
//====================================EndScene_End============================================================================//
//=================================Dip_Start============================================================================================//
typedef HRESULT ( WINAPI* oDrawIndexedPrimitive ) ( LPDIRECT3DDEVICE8 pDevice, D3DPRIMITIVETYPE pType, UINT nMinIndex, UINT nNumVertices, UINT nStartIndex, UINT nPrimitiveCount );
oDrawIndexedPrimitive pDrawIndexedPrimitive;
HRESULT WINAPI myDrawIndexedPrimitive(LPDIRECT3DDEVICE8 pDevice, D3DPRIMITIVETYPE pType, UINT nMinIndex, UINT nNumVertices, UINT nStartIndex, UINT nPrimitiveCount)
{
if(WallHack)
{
texnum = (nNumVertices*100000)+nPrimitiveCount;
if(m_Stride==40 &&
(texnum==7500121 )||(texnum==8500105 )||(texnum==12400168)||(texnum==37000650)||
(texnum==18000274)||(texnum==8800105 )||(texnum==36900650)||(texnum==19600314)||
(texnum==21800306)||(texnum==7500121 )||(texnum==8500105 )||(texnum==12400168)||
(texnum==21800306)||(texnum==36900650)||(texnum==7500121 )||(texnum==37000650)||
(texnum==18000274)||(texnum==7500121 )||(texnum==8500105 )||(texnum==38000658)||
(texnum==22100268)||(texnum==62400752)||(texnum==27900456)||(texnum==45700654)||
(texnum==4800040 )||(texnum==83600752)||(texnum==33400477)||(texnum==38100666)||
(texnum==2800036 )||(texnum==62400752)||(texnum==29700492)||(texnum==84900778)||
(texnum==27500442)||(texnum==52100658)||(texnum==62400752)||(texnum==33600552)||
(texnum==44100646)||(texnum==18000274)||(texnum==37200508)||(texnum==45700654)||
(texnum==37200508)||(texnum==52100658)||(texnum==52100658) &&
(nNumVertices == 100 && nPrimitiveCount == 121) || //Foot
(nNumVertices == 105 && nPrimitiveCount == 168) || //Right Arm
(nNumVertices == 132 && nPrimitiveCount == 180) || //Hand
(nNumVertices == 159 && nPrimitiveCount == 200) || //Left Arm
(nNumVertices == 338 && nPrimitiveCount == 534) || //Underbody thanks japennese guy =)
//(nNumVertices == 448 && nPrimitiveCount == 776) || //Head
(nNumVertices == 804 && nPrimitiveCount == 1016) || //Body //SRG Option item
(nNumVertices == 109 && nPrimitiveCount == 110) || //Bulletproof Vest
(nNumVertices == 336 && nPrimitiveCount == 532)) //Battle Pants
{
pDevice->SetRenderState(D3DRS_ZENABLE, D3DZB_FALSE);
pDevice->SetRenderState(D3DRS_ZFUNC,D3DCMP_NEVER);
pDevice->SetTexture(0,Orange);
//pDevice->SetRenderState(D3DRS_FILLMODE, D3DFILL_WIREFRAME );
pDrawIndexedPrimitive(pDevice, pType, nMinIndex, nNumVertices, nStartIndex, nPrimitiveCount);
//pDevice->SetRenderState(D3DRS_FILLMODE, D3DFILL_SOLID );
pDevice->SetRenderState(D3DRS_ZENABLE, D3DZB_TRUE);
pDevice->SetRenderState(D3DRS_ZFUNC,D3DCMP_LESSEQUAL);
pDevice->SetTexture(0,Pink);
}
if(m_Stride==40 && texnum== 21300174)
{
pDevice->SetRenderState(D3DRS_ZENABLE, D3DZB_FALSE);
pDevice->SetRenderState(D3DRS_ZFUNC,D3DCMP_NEVER);
pDevice->SetTexture(0,Green);//GreenNade
pDrawIndexedPrimitive(pDevice, pType, nMinIndex, nNumVertices, nStartIndex, nPrimitiveCount);
pDevice->SetRenderState(D3DRS_ZENABLE, D3DZB_TRUE);
pDevice->SetRenderState(D3DRS_ZFUNC,D3DCMP_LESSEQUAL);
pDevice->SetTexture(0,Purple);
}
if(nNumVertices == 158 && nPrimitiveCount == 131)
{
pDevice->SetRenderState(D3DRS_ZENABLE, D3DZB_FALSE);
pDevice->SetRenderState(D3DRS_ZFUNC,D3DCMP_NEVER);
pDevice->SetTexture(0,Red);//GreenNade
pDrawIndexedPrimitive(pDevice, pType, nMinIndex, nNumVertices, nStartIndex, nPrimitiveCount);
pDevice->SetRenderState(D3DRS_ZENABLE, D3DZB_TRUE);
pDevice->SetRenderState(D3DRS_ZFUNC,D3DCMP_LESSEQUAL);
pDevice->SetTexture(0,Yellow);
}
if (nNumVertices == 171 && nPrimitiveCount == 143)
{
pDevice->SetRenderState(D3DRS_ZENABLE, D3DZB_FALSE);
pDevice->SetRenderState(D3DRS_ZFUNC,D3DCMP_NEVER);
pDevice->SetTexture(0,Red);//GreenNade
pDrawIndexedPrimitive(pDevice, pType, nMinIndex, nNumVertices, nStartIndex, nPrimitiveCount);
pDevice->SetRenderState(D3DRS_ZENABLE, D3DZB_TRUE);
pDevice->SetRenderState(D3DRS_ZFUNC,D3DCMP_LESSEQUAL);
pDevice->SetTexture(0,Yellow);
}
if(m_Stride==40 &&//face,mask etc...
(texnum==36700612) ||
(texnum==9600172 ) ||
(texnum==14200236) ||
(texnum==37800552) ||
(texnum==28100486) ||
(texnum==35500568) ||
(texnum==2200024 ) ||
(texnum==16200243) ||
(texnum==31900466) ||
(texnum==19300342) ||
(texnum==36200604) ||
(texnum==21300290) ||
(texnum==35700558) ||
(texnum==22100396) ||
(texnum==36100604) ||
(texnum==27100464) ||
(texnum==11400180) ||
(texnum==34900580) ||
(texnum==13200212) ||
(texnum==34700538) ||
(texnum==19500352)&&
(nNumVertices == 448 && nPrimitiveCount == 776))
{
pDevice->SetTexture(0,Blue);
}
{
pDevice->SetRenderState(D3DRS_FOGENABLE,false);
}
/*Logger
if(m_Stride==40){
while(GetAsyncKeyState(VK_NUMPAD1)&1) arrc--; //Used as manual index for adding textures to delarray
while(GetAsyncKeyState(VK_NUMPAD3)&1) arrc++;
bool alrdy=false;
bool inarr=false;
if(texarray[arrc]==texnum)
if(delarray[i]==texarray[arrc])
alrdy=true;
for(int i=0;i<dcount;i++) //sees if said texture is in delarray
if(delarray[i]==texnum)
inarr=true;
if(texarray[arrc]==texnum || inarr){ //If true, color model differently
LPDIRECT3DTEXTURE8 texCol;
DWORD dwOldZEnable = D3DZB_TRUE;
pDevice->SetTexture(0, NULL);
pDevice->GetRenderState(D3DRS_ZENABLE, &dwOldZEnable);
pDevice->SetRenderState(D3DRS_ZENABLE, D3DZB_FALSE);
if(alrdy) //Different colors for selected models that are already being logged (For removal from array)
texCol=Blue;
else
texCol=Red;
pDevice->SetTexture(0, texCol);
pDrawIndexedPrimitive(pDevice, pType, nMinIndex, nNumVertices, nStartIndex, nPrimitiveCount);
pDevice->SetRenderState(D3DRS_ZENABLE, dwOldZEnable);
}
}
if(GetAsyncKeyState(VK_F5)&1) add_log("Logged tesx: %i", texarray[arrc]); //F5 will print currently selected texnum to logfile
if(GetAsyncKeyState(VK_F6)&1) { //For adding/removing textures to array
bool inarr=true;
for(int k=0;k<dcount;k++){
if(delarray[k]==texarray[arrc])
{
inarr=false;//Found selected texture to already exist
delarray[k]=0;//Delete texture
break;//Cancel loop
}
}
if(inarr==true)
{
delarray[dcount]=texarray[arrc];//Add texture
dcount++;
}
}
if(GetAsyncKeyState(VK_F7)&1){
int total=1;
add_log("omfg values?!? {");
for(int x=0;x<dcount;x++)//Loops through all recorded variables and prints them in a nice array based format
if(delarray[x]){
add_log("%i,",delarray[x]); //add_log2==add_log but without endl
total++;
}
add_log("}; %i variables in array",total);
}
bool found = false; //THIS PART CREDITS TO KRYPTEC
for(int y=0; y<arraycounter; y++) //THIS IS HIS LOGGING FUNCTION
{
if(texnum==texarray[y])found=true; //I JUST CREATED AN INTERFACE FOR IT
}
if(!found && arraycounter < 1000)
{
texarray[arraycounter]=texnum;
arraycounter++;
}*/
}
return pDrawIndexedPrimitive(pDevice, pType, nMinIndex, nNumVertices, nStartIndex, nPrimitiveCount);
}
//=====================================Dip_End===========================================================================//
//=====================================Sss_Start==========================================================================//
typedef HRESULT ( WINAPI* oSetStreamSource ) ( LPDIRECT3DDEVICE8 pDevice, UINT nStreamNumber, LPDIRECT3DVERTEXBUFFER8 pStreamData, UINT nStride );
oSetStreamSource pSetStreamSource;
HRESULT WINAPI mySetStreamSource(LPDIRECT3DDEVICE8 pDevice, UINT nStreamNumber, LPDIRECT3DVERTEXBUFFER8 pStreamData, UINT nStride)
{
if(nStreamNumber==0)
m_Stride = nStride;
return pSetStreamSource(pDevice, nStreamNumber, pStreamData, nStride);
}
//====================================Sss_End============================================================================//
//====================================Svp_Start==========================================================================//
typedef HRESULT (WINAPI* oSetViewport)(LPDIRECT3DDEVICE8 pDevice,CONST D3DVIEWPORT8* pViewport);
oSetViewport pSetViewport;
HRESULT WINAPI mySetViewport(LPDIRECT3DDEVICE8 pDevice,CONST D3DVIEWPORT8* pViewport)
{
ScreenCenterX = ( float )pViewport->Width / 2;
ScreenCenterY = ( float )pViewport->Height / 2;
return pSetViewport(pDevice,pViewport);
}
//===================================Svp_End=============================================================================//
typedef HRESULT ( WINAPI* oBeginScene ) ( LPDIRECT3DDEVICE8 pDevice );
oBeginScene pBeginScene;
HRESULT WINAPI myBeginScene(LPDIRECT3DDEVICE8 pDevice)
{
if((GetAsyncKeyState(VK_F6)&1))
{
pEndScene = (oEndScene)DetourFunction((PBYTE)dwEndScene, (PBYTE)myEndScene);
pDrawIndexedPrimitive = (oDrawIndexedPrimitive)DetourFunction((PBYTE)dwDrawIndexedPrimitive, (PBYTE)myDrawIndexedPrimitive);
pSetStreamSource = (oSetStreamSource)DetourFunction((PBYTE)dwSetStreamSource, (PBYTE)mySetStreamSource);
pSetViewport=(oSetViewport)DetourFunction((PBYTE)dwSetViewport,(PBYTE)mySetViewport);
}
return pBeginScene(pDevice);
}
BOOL WINAPI DllMain ( HMODULE hModule, DWORD dwReason, LPVOID lpReserved )
{
DisableThreadLibraryCalls(hModule);
if ( dwReason == DLL_PROCESS_ATTACH )
{
//=========Log==========================//
GetModuleFileName(hModule, dlldir, 512);
for(int i = strlen(dlldir); i > 0; i--) { if(dlldir[i] == '\\') { dlldir[i+1] = 0; break; } }
ofile.open(GetDirectoryFile("log.txt"), ios::app);
//=========Log=========================//
pBeginScene = (oBeginScene)DetourFunction((PBYTE)dwBeginScene, (PBYTE)myBeginScene);
pEndScene = (oEndScene)DetourFunction((PBYTE)dwEndScene, (PBYTE)myEndScene);
pDrawIndexedPrimitive = (oDrawIndexedPrimitive)DetourFunction((PBYTE)dwDrawIndexedPrimitive, (PBYTE)myDrawIndexedPrimitive);
pSetStreamSource = (oSetStreamSource)DetourFunction((PBYTE)dwSetStreamSource, (PBYTE)mySetStreamSource);
pSetViewport=(oSetViewport)DetourFunction((PBYTE)dwSetViewport,(PBYTE)mySetViewport);
}
return TRUE;
}
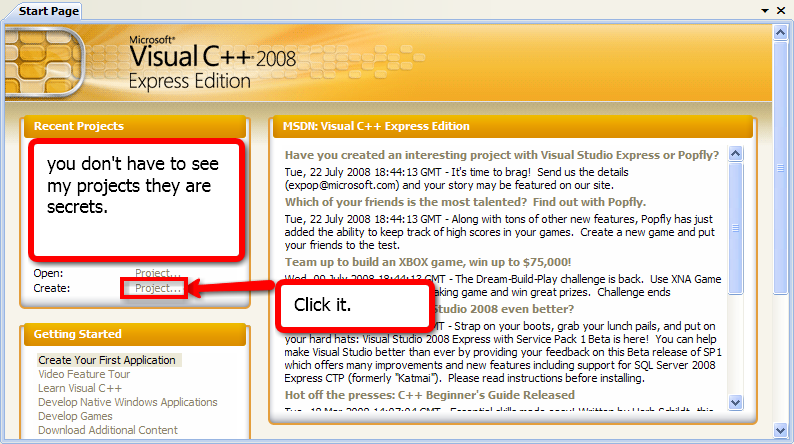
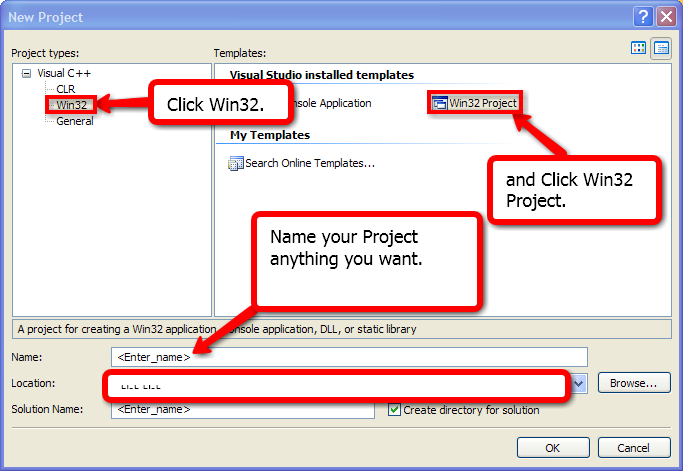
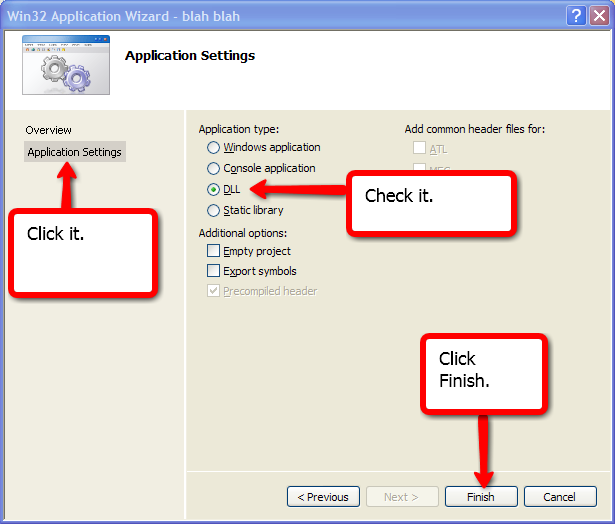
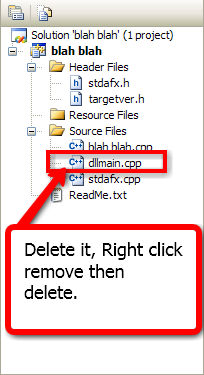
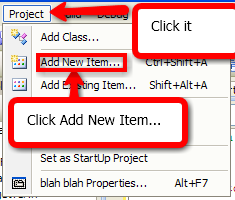
17. You will find your DLL file in C:\Documents and
Settings\TheIFear\My Documents\Visual Studio 2008\Projects\(name of
your dll)\Debug, and you will find your dll.



 del.icio.us
del.icio.us Digg It!
Digg It! yahoo
yahoo Facebook
Facebook rss
rss




1 • Gabry
April 21, 2008 at 8:37 am
Hello was reading your page about the htaccess file to block proxy servers from surfing my site, very interesting, but my host said that since I use FrontPage editor it might block me from editing my site, is there a way to avoid this? Thank you in advance