php test : download
http://shat.net/php/nqt/nqt.php.txt.
copy this file under /var/www/html
visit http://yourwebsite
if you see network query tool window and execute some command over there, your php works fine.
cd /root
mkdir snortinstall
!!!DO THE FOLLOWING AS ROOT!!!
download your snort
wget
http://www.snort.org/dl/snort-2.8.3.1.tar.gz
install PCRE from source
wget
http://downloads.sourceforge.net/pcre/pcre-7.8.tar.gz?modtime=1220617433&big_mirror=0
tar xvzf pcre-7.8.tar.gz
cd pcre-7.8
./configure
make
make install
cd back to your snortinstall dir
tar xvzf snort-2.8.3.1.tar.gz
cd snort-2.8.3.1
./configure --with-mysql --enable-dynamicplugin --with-libpcap-libraries=/usr/lib64 --with-libpcre-libraries=/usr/lib64 --with-libnet-libraries=/usr/lib64 --enable-stream4udp --enable-dynamicplugin LDFLAGS='-L/usr/lib64 -L/usr/lib64 -L/usr/lib64 -L/usr/lib64/mysql'
make
make install
groupadd snort
useradd -g snort snort -s /sbin/nologin
mkdir /etc/snort
mkdir /etc/snort/rules
mkdir /var/log/snort
cd /etc
cp * /etc/snort
wget
http://www.snort.org/pub-bin/downloads.cgi/Download/vrt_pr/snortrules-pr-
2.4.tar.gz
or just download my previous uploaded snortrules-snapshot-2.8.tar.gz
tar xvzf snortrules-pr-2.4.tar.gz
or tar xvzf snortrules-snapshot-2.8.tar.gz
cd to rules and do the following command
cp -R * /etc/snort/rules
Modify your snort.conf file
edit snort.conf under /etc/snort by using vi or any other editor
change followings
var HOME NET 10.0.0.0/8 (for example)
var EXTERNAL_NET !$HOME_NET
var RULE_PATH ../rules to var RULE_PATH /etc/snort/rules
add or edit as followings
preprocessor stream5_global: max_tcp 8192, track_tcp yes, \
track_udp yes
preprocessor stream5_tcp: policy windows, use_static_footprint_sizes, \
ports client 21 23 25 42 53 80 135 136 137 139 143 110 111 445 465 513 691 1433 1521 2100 2301 3128 3306 8000 8080 8180 8888
preprocessor stream5_udp: ignore_any_rules
also, you need to tell snort to log to MySQL
output database: log, mysql, user=snort password=<the password you gave it>
dbname=snort host=localhost
cd /etc/init.d
wget http://internetsecurityguru.com/snortinit/snort/index.html
mv index.html snort
chmod 755 snot
chkconfig snort on
mysql -p
passwd:
(default: whatever password you wawnt to give it, remember what you assign.)
mysql
mysql> SET PASSWORD FOR
root@localhost=PASSWORD('password');
>Query OK, 0 rows affected (0.25 sec)
mysql> create database snort;
>Query OK, 1 row affected (0.01 sec)
mysql> grant INSERT,SELECT on root.* to
snort@localhost;
>Query OK, 0 rows affected (0.02 sec)
mysql> SET PASSWORD FOR
snort@localhost=PASSWORD('password_from_snort.conf');
>Query OK, 0 rows affected (0.25 sec)
mysql> grant CREATE, INSERT, SELECT, DELETE, UPDATE on snort.* to
snort@localhost;
>Query OK, 0 rows affected (0.02 sec)
mysql> grant CREATE, INSERT, SELECT, DELETE, UPDATE on snort.* to snort;
>Query OK, 0 rows affected (0.02 sec)
mysql> exit
>Bye
mysql -u root -p < ~/snortinstall/snort-2.4.3/schemas/create_mysql snort
Enter password: the mysql root password
mysql -p
>Enter password:
mysql> SHOW DATABASES;
(You should see the following)
+------------+
| Database
+------------+
| mysql
| Snort
| test
+------------+
3 rows in set (0.00 sec)
mysql> use snort
>Database changed
mysql> SHOW TABLES;
+------------------+
| Tables_in_snort
+------------------+
| data
| detail
| encoding
| event
| icmphdr
| iphdr
| opt
| reference
| reference_system
| schema
| sensor
| sig_class
| sig_reference
| signature
| tcphdr
| udphdr
+------------------+
16 rows
exit;
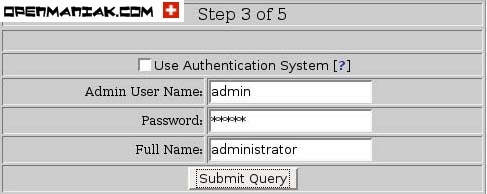
BASE-Install
yum install php-gd
It will ask you the following, choose Y
Transaction Listing:
Install: php-gd.i386 0:4.3.10-3.2
Is this ok [y/N]: y
download adodb
wget
http://downloads.sourceforge.net/adodb/adodb505.tgz?modtime=1215766049&big_mirror=0
adodb505.tga
download attached above base file
cd /etc/sysconfig/
edit the iptables file
add the line “-A RH-Firewall-1-INPUT -m state --state NEW -m tcp -p tcp --dport 443 -j
ACCEPT
And delete the lines:
-A RH-Firewall-1-INPUT -p 50 -j ACCEPT
-A RH-Firewall-1-INPUT -p 51 -j ACCEPT
-A RH-Firewall-1-INPUT -p udp --dport 5353 -d 224.0.0.251 -j ACCEPT
-A RH-Firewall-1-INPUT -p udp -m udp --dport 631 -j ACCEPT
-A RH-Firewall-1-INPUT -m state --state NEW -m tcp -p tcp --dport 80 -j ACCEPT
Then change the line :
-A RH-Firewall-1-INPUT -p icmp --icmp-type any -j ACCEPT
To :
-A RH-Firewall-1-INPUT -p icmp --icmp-type any -j REJECT
Then you will only be able to get to the site with HTTPS:// the reason you want to do this
is so you do not trigger more alerts from you reading alerts, and if something is able to be
encrypted then I usually do.
Then execute the command “service iptables restart” and you will see something like tee following:
[root@snort conf]# service iptables restart
Flushing firewall rules: [ OK ]
Setting chains to policy ACCEPT: filter [ OK ]
Unloading iptables modules: [ OK ]
Applying iptables firewall rules: [ OK ]
Then it will look like this when you do an “iptables –L”
Installing Adodb:
Go back to your download directory (~/snortinstall)
cp adodb462.tgz /var/www/
cd /var/www/
tar -xvzf adodb462.tgz
rm –rf adodb462.tgz
Go back to your download directory (~/snortinstall)
cp base-1.2.5.tar.gz /var/www/html
cd /var/www/html
tar xvzf base-1.2.5.tar.gz
rm -rf base-1.2.5.tar.gz
mv base-1.2.5 base
cd /var/www/html/base
cp base_conf.php.dist base_conf.php
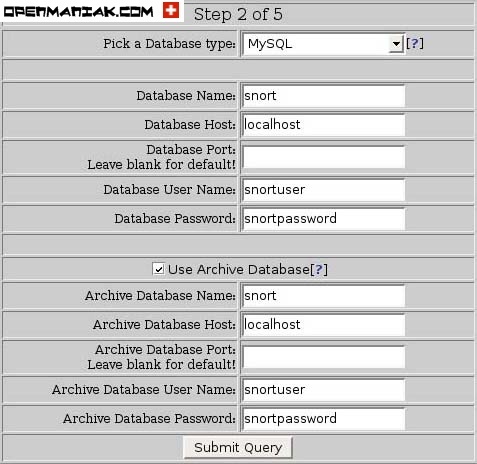
edit the "base_conf.php" file and insert the following perimeters
$BASE_urlpath = "/base";
$DBlib_path = "/var/www/adodb/ ";
$DBtype = "mysql";
$alert_dbname = "snort";
$alert_host = "localhost";
$alert_port = "";
$alert_user = "snort";
$alert_password = "password_from_snort_conf";
/* Archive DB connection parameters */
$archive_exists = 0; # Set this to 1 if you have an archive DB
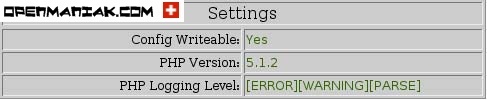
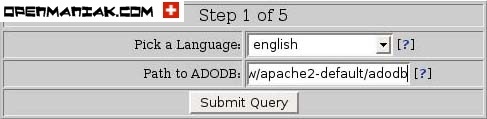
Now, go to a browser and access your sensor.
NOW: “chkconfig snort on” to make snort starts with the system
then type service snort start. It should give you an OK
https://<ip.address>/base
This will bring up the initial BASE startup banner.
Securing APACHE and the BASE directory:
mkdir /var/www/passwords
/usr/bin/htpasswd -c /var/www/passwords/passwords base
(base will be the username you will use to get into this directory, along with the password
you choose)
It will ask you to enter the password you want for this user, this is what you will have to
type when you want to view your BASE page
Edit the httpd.conf (/etc/httpd/conf). I put it under the section that has:
<Directory />
Options FollowSymLinks
AllowOverride None
</Directory>
These are the lines you must add to password protect the BASE console, add it to
the httpd.conf file in /etc/httpd/conf/:
<Directory "/var/www/html/base">
AuthType Basic
AuthName "SnortIDS"
AuthUserFile /var/www/passwords/passwords
Require user base
</Directory>
Since you have removed the port 80 entry in the iptables script you will have to go to the
console on port 443, using HTTPS:/<ip_address>/base
Save the file and restart Apache by typing “service httpd restart” to make the password
changes effective.
After you’re done
Login as root and check everything important to see if it is running.
To check you can execute “ps –ef |grep <SERVICE>” where service is snort. httpd, or
mysql.
Or use “ps –ef |grep httpd && ps –ef |grep mysql && ps –ef |grep Snort”
or visit
http://www.howtoforge.com/intrusion_detection_base_snort



 snortrules-snapshot-2.8.tar.gz
snortrules-snapshot-2.8.tar.gz Snort_and_BASE_on_CentOS_RHEL_or_Fedora.pdf
Snort_and_BASE_on_CentOS_RHEL_or_Fedora.pdf

