How to compare two Excel sheets for differences in values
It is the simplest way to compare data in Excel that lets you identify cells with different values. As the result, you will have a difference report in a new worksheet.
To compare two Excel worksheets for differences, just open a new empty sheet, enter the following formula in cell A1, and then copy it down and to the right:
=IF(Sheet1!A1<> Sheet2!A1, "Sheet1:"&Sheet1!A1&" vs Sheet2:"&Sheet2!A1, "")
The result will look similar to this: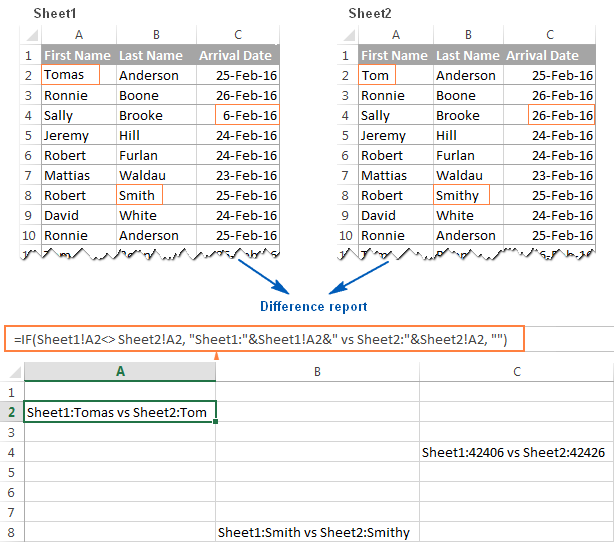
As you can see in the above screenshot, the formula compares 2 sheets, identifies cells with deferent values and displays the differences in corresponding cells. Please note that in the difference report, dates (cell C4) are presented by serial numbers as they are stored in the internal Excel system, which is not very convenient for analyzing differences between them.
Highlight differences between 2 sheets with conditional formatting
To highlight cells that have different values in two sheets with the color of your choosing, use the Excel conditional formatting feature:
- In the worksheet where you want to highlight differences, select all used cells. For this, click the upper left cell of the used range, usually A1, and press Ctrl + Shift + End to extend the selection to the last used cell.
- On the Home tab, in the Styles group, click Conditional Formatting > New rule, and create a rule with the following formula:
=A1<>Sheet2!A1Where Sheet2 is the name of the other sheet you are comparing.
As the result, the cells with different values will get highlighted with the selected color: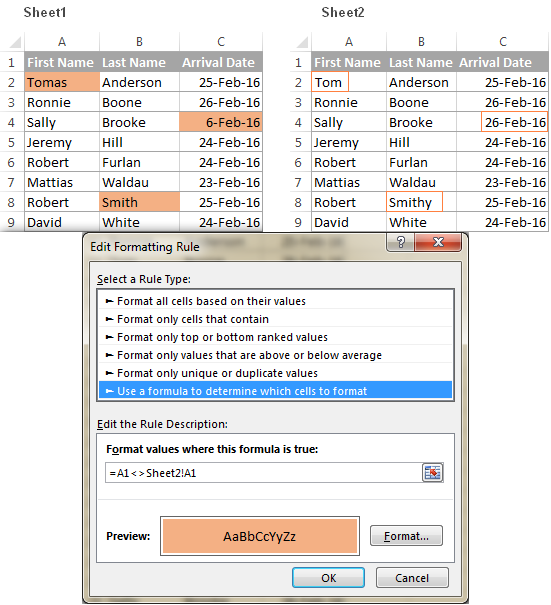
If you are not very familiar with Excel conditional formatting, you can find the detailed steps to create a rule in the following tutorial: Excel conditional formatting based on another cell value.
As you see, it's very easy to compare two Excel sheets by using formulas or conditional formats. However, these methods are not well suited for all-round comparison because of the following limitations:
- They find differences only in values, but cannot compare formulas or cell formatting.
- They cannot identify added or deleted rows and columns. As soon as you add or delete a row / column in one sheet, all subsequent rows / columns will be marked as differences.
- They work on a sheet level, but cannot detect workbook-level structural differences such as sheet additions and deletions.
Compare and merge copies of a shared workbook
When it comes to merging different versions of the same Excel file, the Compare and Mergefeature comes in handy. It is especially useful when several users collaborate on the same Excel workbook because it lets you view the changes and comments of all users at a time. To leverage this feature, be sure to do the following preparations:
- Share your Excel workbook before you make it available to other users.
To share a workbook, just click the Share Workbook button on the Review tab, in the Changesgroup, select the Allow Changes by More Than One User...box, and click OK. Allow Excel to save the workbook if prompted. Turning on the Track Changes feature shares the workbook automatically.
- Each person who makes any edits to the shared workbook must save a copy (.xls or xlsx file) using a unique file name.
Now that all initial preparations are done properly, you are ready to combine the copies of a shared workbook.
1. Enable the Compare and Merge Workbooks feature in your Excel
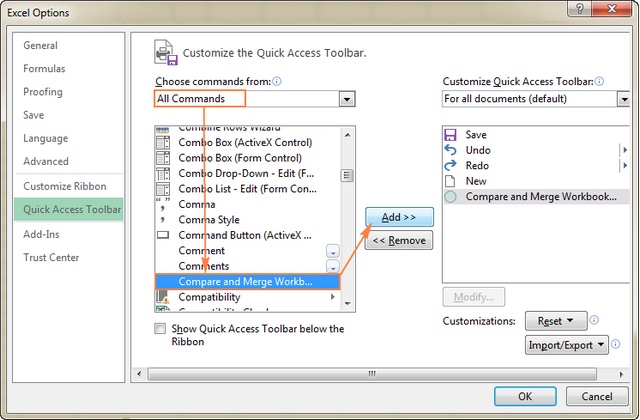
Although, the Compare and Merge Workbooks feature is available in all versions of Excel 2016, Excel 2013, Excel 2010 and lower, this command is not displayed anywhere in Excel by default. To add it to the Quick Access toolbar, perform the following steps:
- Open the Quick Access drop down menu and select More Commands.
- In the Excel Options dialog box, select All Commands under Choose commands from.
- In the list of commands, scroll down to Compare and Merge Workbooks, select it and click theAdd button to move it to the right-hand section.
- Click OK.
2. Compare and merge workbooks
When all of the users have finished working with your shared Excel workbook, you can merge all the copies into one file.
- Open the primary version the shared workbook.
- Click the Compare and Merge Workbooks command on the Quick Access toolbar.

- In the dialog box that appears, select a copy of the shared workbook that you want to merge. To select several copies, hold the Shift key while clicking the file names, and then click OK.

Done! The changes from each copy are merged into a single workbook, and you can review all the edits at a time. To point out the row and columns with differences, Excel highlights the column letters and row numbers in a dark red color. At the cell level, edits from different users are marked with different colors, so you can see at a glance who made a particular change.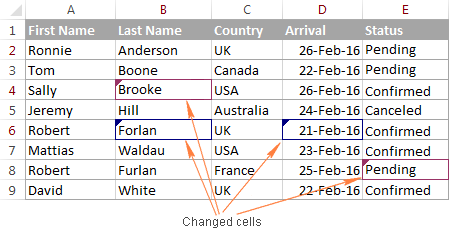
Note. If the Compare and Merge Workbooks command is greyed out in your Excel, most likely you are trying to combine different Excel files. Please remember, the Compare and Merge Workbooks feature allows merging only copies of the same shared workbook.
Third-party tools to compare Excel files
As you have just seen, Microsoft Excel provides a handful of features to compare data in two or more workbooks. But none of the built-in options is sufficient to comprehensively compare Excel sheets, let alone entire workbooks, spotting all the differences in values, formulas or formatting.
So, if you need advanced and really efficient means to compare two Excel files, then most likely you would have to use one of the third-party tools specially designed for comparing, updating and merging Excel sheets and workbooks. Below you will find a quick overview of a few tools that, in my opinion, are best performers in this area.
Synkronizer Excel Compare: 3-in-1 tool to compare, merge and update Excel files
The Synkronizer Excel Compare add-in can quickly compare, merge and update two Excel files saving you the trouble of searching for differences manually.
If you are looking for a quick and reliable method to compare two Excel sheets or workbooks, you will certainly find helpful the following features of Synkronizer Excel Compare:
- Identifying the differences between two Excel sheets.
- Combining multiple Excel files into a single version without producing unwanted duplicates.
- Highlighting the differences in both sheets.
- Showing only the differences that are relevant to your task.
- Merging and updating the sheets.
- Presenting detailed and easy to read difference reports.
To get some basic idea about Synkronizer Excel Compare's capabilities and performance, let's carry out a couple of field tests.
Compare two Excel files for differences
Supposing you are organizing some event and, in your Excel table, you gather information about the participants such as a participant name, arrival date, number of seats and other details. Also, you have a couple of managers in direct contact with participants and the database, and as a result, you have 2 versions of the same Excel file.
Okay, let's see how efficiently Synkronizer can compare our two sheets and identify differences between them.
To run Synkronizer Excel Compare, go to the Add-ins tab, and click the Synchronizer 11 icon.
The Synkronizer pane will show up in the left part of your Excel window, where you perform 5 quick steps:
- Select 2 workbooks to compare:
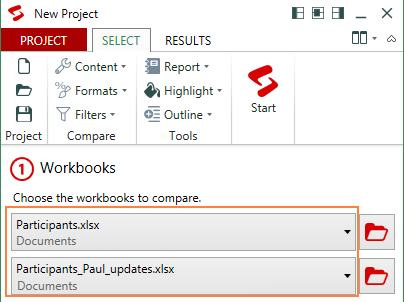
- Select sheets to compare.
If the selected workbooks have any sheets with the same names, all those sheets will be matched and automatically selected for comparison (like Participants sheets in the below screenshot).
Also, you can manually select worksheets you want to compare, or instruct the add-in to match sheets by other criteria, for example by worksheet type - all, protected, or hidden.
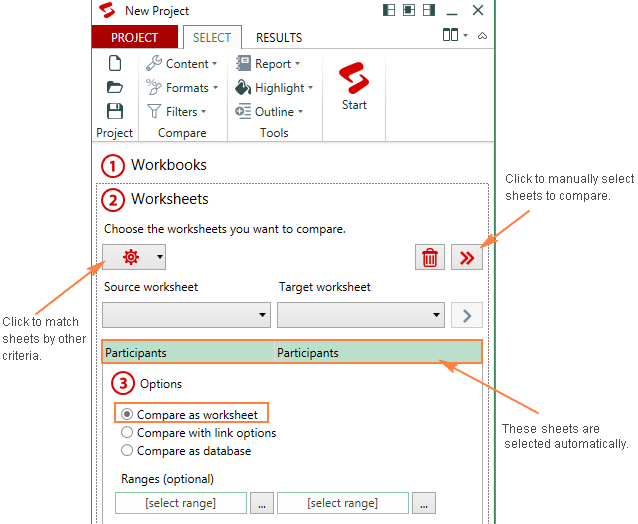
Once you've selected the sheets, the Synkronizer add-in will open them side by side, arranged vertically or horizontally, like in Excel's View Side by Side mode.
- Select one of the following comparison options:
- Compare as normal worksheets - the default option that works in most cases.
- Compare with link options - if the selected sheets do not contain any new or deleted rows and columns, you can compare them "1 on 1".
- Compare as database - recommended for comparing sheets that have a database structure.
- Compare selected ranges - if you do not want to compare the entire sheets, define the ranges to be compared.
- Choose the content types to be compared (optional).
On the Select tab, in the Compare group, you can choose the content type(s) relevant to your current task:

- Under Content, you can select comments and names (in addition to cell values, formulas and calculated values that are compared by default).
- Under Formats, you choose what cell formats such as alignment, fill, font, border etc.
- The Filters option lets you filter out differences that you don't want to display. For example, you can ignore case, leading or trailing spaces, all formulas or different formulas with the same result, hidden rows or column, and more.
- Finally, click the big red Start button on the ribbon and proceed to examining the results.
Visualizing and analyzing the differences
Usually it takes Synkronizer only a few seconds to compare 2 sheets and present a brief summary report and detailed difference report on the Results tab.
In a summary report, you can see all difference types at a glance: changes in columns, rows, cells, comments, formats, and names.
To view the detailed difference report, just click a specific difference type on the summary report.
The following screenshot shows the summary report (in the upper part of the Results pane), and cell difference report (in the lower part of the pane) that were created for our sample sheets: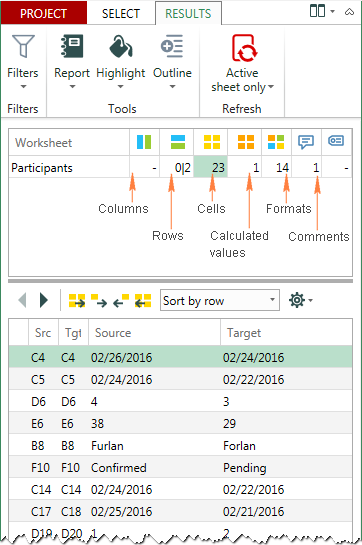
As soon as you click on a difference, you will immediately be taken to the corresponding cells on both sheets you are comparing (the below screenshot shows just one sheet because there's enough room on this page to show both :)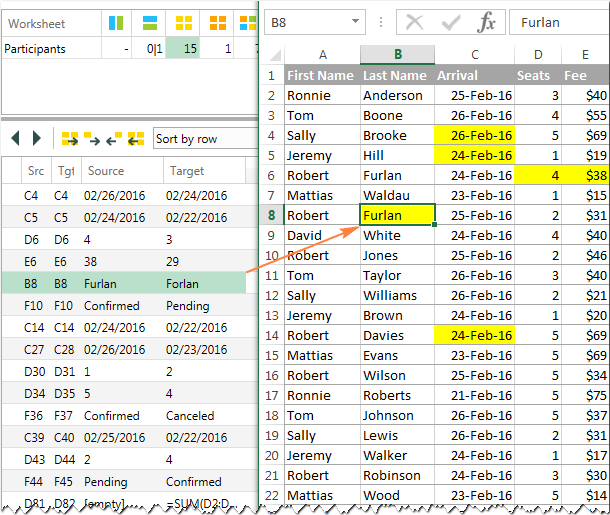
In addition, you can create a difference repot in a separate workbook, either standard or hyperlinked, and jump to a specific difference with a mouse click: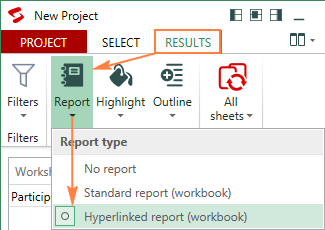
Compare all sheets in two workbooks at a time
If the two Excel files you are comparing contain multiple sheets, all matching worksheet pairs will be presented in the summary report for your perusal: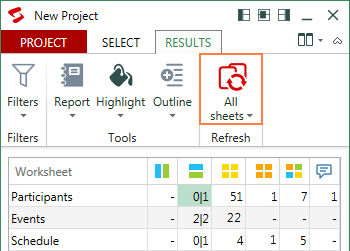
Highlighting differences between sheets
By default, the Synkronizer Excel Compare add-in highlights all found differences, like in the following screenshot:
- Yellow - differences in cell values
- Lilac - differences in cell formats
- Green - inserted rows
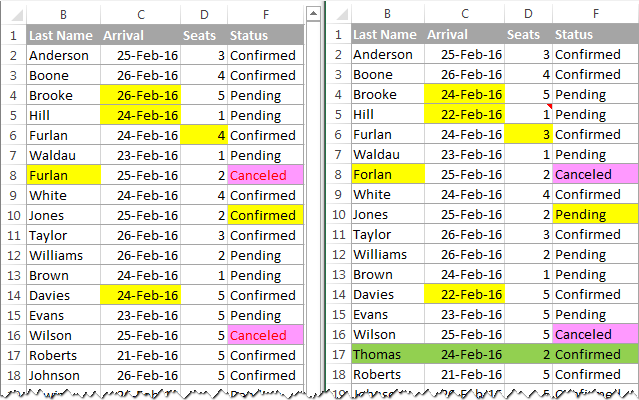
To highlight only the relevant differences, click the Outline button on the Results tab, and select the required options: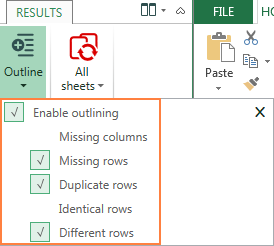
Update and merge sheets
The merge function is definitely one of the most useful functions of the Synkronizer Excel Compare add-in. It lets you transfer values from sheet 1 to sheet 2 and vice versa. You can merge individual cells values or move different columns/rows from the source to target sheet, and have your primary sheet updated in seconds.
To update one or more differences, select them on the Synkronizer's pane and click one of the 4 update buttons - the first and last buttons update all differences, while the 2nd and 3rd buttonsupdate selected differences only (the button arrows indicate the transfer direction):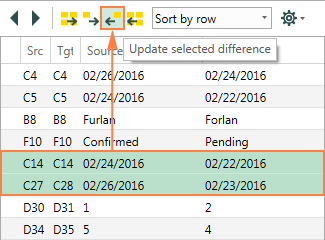
Well, these are the key features of the Synkronizer add-in, but there is certainly much more to it. If you are curious to give it a shot, here's a trial version.
In my opinion, Synkronizer is one of the best tools to compare files in Excel, but it's not the only option available to you. A handful of other comparison tools exist, which basically provide the same set of features in different implementations.
xlCompare: compare and merge workbooks, sheets and VBA projects
Using the xlCompare utility, you can compare two Excel files, worksheets, names and VBA Projects. It identifies added, deleted and changed data and allows you to quickly merge differences. In addition, it provides the following options:
- Find duplicate records between two worksheets and remove them.
- Update all existing records in one sheet with values from another sheet.
- Add unique (new) rows and columns from one sheet to another.
- Merge all updated records from one workbook to another.
- Sort data on the sheets by the key column.
- Filter the comparison results to display differences or identical records.
- Highlight comparison results with colors.
Florencesoft DiffEngineX: compare Excel workbooks for differences
DiffEngineX is another utility that can help you identify differences between cell values, formulas, comments, Excel names, and VBA code. It can compare two Excel workbooks or selected sheets.
DiffEngineX works with xls, xlsx, xlsm and xlsb files, and supports Excel 2013, Excel 2010, Excel 2007 and Excel 2003.
Change pro for Excel: compare Excel sheets on desktop and mobile devices
With Change pro for Excel, you can compare two sheets in desktop Excel as well as on mobile devices with optional server-based comparison. The key features of this tool are:
- Find differences between 2 sheets in formulas and values.
- Identify layout changes, including added / deleted rows and columns.
- Recognize embedded objects such as charts, graphs and images.
- Create and print difference reports of formula, value and layout differences.
- Filter, sort, and search the difference report on key changes.
- Compare files directly from Outlook or document management systems.
- Support for all languages, including multi-byte.
Online services to compare Excel files
Apart from desktop tools and utilities, there exist a number of online services that let you quickly compare two Excel sheets for differences without installing any software on your computer. Probably it's not the best solution in terms of security, but if your Excel files do not contain any sensitive information why not use some free online service for immediate results?
For example, you can try XLComparator or CloudyExcel, or find some other similar services on the net. This is how the CloudyExcel service looks like:
You just upload the two Excel workbooks you want to compare, and click the Find Differencebutton at the bottom of the screen. In a moment, the differences in two active sheets will get highlighted with different colors: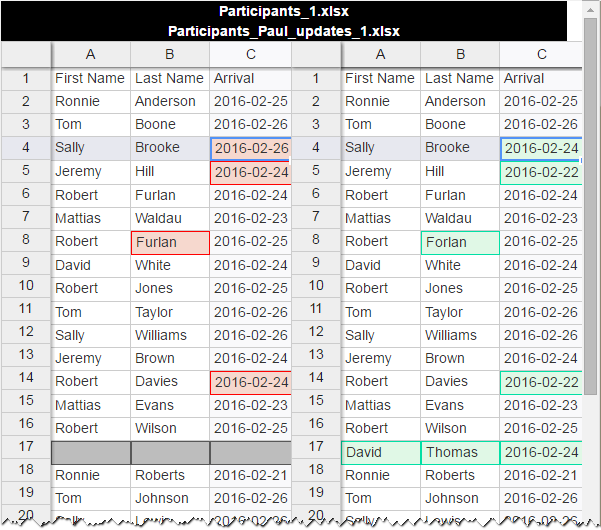
Well, this is how you can compare Excel files for differences. If none of the solutions described in this tutorial is suitable for your task, check out the following resources that cover other aspects of Excel file comparison. And if you know any other ways to compare two Excel files, your comments will be greatly appreciated. I thank you for reading and hope to see you on our blog next week!
Other ways to compare and merge data in Excel
'IT' 카테고리의 다른 글
| basketball (0) | 2012.11.01 |
|---|---|
| The Best AirPrint Compatible Printers (0) | 2011.12.23 |
| Setting the secure flag in the cookie is easy (0) | 2011.12.10 |
| Why Java Will Always Be Slower than C++ (0) | 2011.12.09 |
| a (0) | 2011.12.09 |
 Sandro Gauci
Sandro Gauci


