Once Snort is installed, It is required to install the Snort signature rules and keep them up-to-date.
By chance, there is a perl script that will give us some precious help: Oinkmaster.
| #apt-get install oinkmaster |
 Install or update the rules.
Install or update the rules.To downlaod the Snort rules, we need to create a free account on the Snort website.
The Snort rules are made by Sourcefire and you can get them for free a few days after the commercial subscription release.
Once you are logged into your Snort account, you can get a code at the bottom of the page.
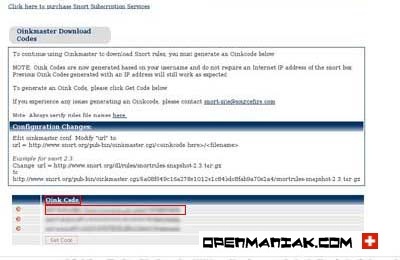 |
We need this code in the /etc/oinkmaster.conf file.
You need first to know which Snort version you have:
| # snort -V |
,,_ -*> Snort! <*-
o" )~ Version 2.3.2 (Build 12)
'''' By Martin Roesch & The Snort Team: http://www.snort.org/team.html
(C) Copyright 1998-2004 Sourcefire Inc., et al.
Modify the "url" settings in the /etc/oinkmaster.conf file as below:
| url = http://www.snort.org/pub-bin/oinkmaster.cgi/yourcode_here/ snortrules-snapshot-2.3.tar.gz |
If you have a 2.6.x Snort version, you need to configure the "url" setting as below:
| url = http://www.snort.org/pub-bin/oinkmaster.cgi/yourcode_here/ snortrules-snapshot-CURRENT.tar.gz |
| #mkdir /etc/snort/backup |
So let's add a user called oinkmaster.
| #useradd oinkmaster |
| #chown -R oinkmaster /etc/snort/backup #chown -R oinkmaster /etc/snort/rules #chown -R oinkmaster /var/run/oinkmaster #chmod 644 /etc/snort/snort.conf |
| #su oinkmaster oinkmaster#oinkmaster -o /etc/snort/rules -b /etc/snort/backup 2>&1 |
Here is a example of our backup folder after running oinkmaster:
| #dir /etc/snort/backup |
 The crontab
The crontabSince we are quite lazy, we don't want to manually run this script every day.
A little cron will help us.
| crontab -e -u oinkmaster 30 00 * * * oinkmaster -o /etc/snort/rules -b /etc/snort/backup 2>&1 >> /dev/null 2>&1 |
(The crontab command will update the /var/spool/cron/crontabs/oinkmaster file)
crontab -e will open nano by default. If you want to open vi instead just type:
#export EDITOR=vi
'Hacking' 카테고리의 다른 글
| Malware Analysis (0) | 2010.04.23 |
|---|---|
| Computer Security Consulting (0) | 2010.04.02 |
| BASE 2010.3.3. Wed (1) | 2010.03.04 |
| Snort IDS Installation (0) | 2010.03.04 |
| TMAC V5 R3 MAC CHANGE (0) | 2009.11.20 |













